[full-post]

How to Install a Mail Server with PostfixAdmin on Ubuntu 20.04
In this tutorial, we’ll be covering the process of setting up a mail
server with Postfix, Dovecot, Postfixadmin and MariaDB on an Ubuntu 20.04 VPS. But first, what is PostfixAdmin?
 PostfixAdmin
is an open-source web-based application written in PHP that’s used to
create virtual domains and email accounts for a Postfix mail server.
Using PostfixAdmin, we can manage mailboxes & aliases, set quotas,
configure vacation/out-of-the-office messages, and more. Plus, the
web-based interface gives you the user-friendliness of a browser window
with a UI.
PostfixAdmin
is an open-source web-based application written in PHP that’s used to
create virtual domains and email accounts for a Postfix mail server.
Using PostfixAdmin, we can manage mailboxes & aliases, set quotas,
configure vacation/out-of-the-office messages, and more. Plus, the
web-based interface gives you the user-friendliness of a browser window
with a UI.
PostfixAdmin allows us to use virtual email addresses and virtual
mailboxes, so we do not need to create a new system user account for
each email address. Considering all of these details, PostfixAdmin is a
versatile tool and can be used for almost all of your mailing needs.
This tutorial goes quite in-depth and may take some time to configure
everything properly. Let’s get started with the installation steps.
Hardware/Software Requirements
- An Ubuntu 20.04 server or VPS with root access enabled, or a user with sudo privileges. We provide all of our users will full root access on their VPSes.
- Postfix mail transfer agent (MTA) and Dovecot IMAP/POP3 Mail Delivery Agent need to be installed.
- A database server (MySQL/MariaDB, PostgreSQL or SQLite) needs to be installed.
- Apache web server needs to be installed with the
mod_rewrite module enabled. - PHP 7.1 or greater must be installed with the
imap, mbstring and mysql extensions all enabled.
Step 1. Getting Started
To begin, we’re going to need to log into our server using SSH. You can do that by entering this command:
ssh root@IP_Address -p Port_Number
Remember to replace “root” with your username if you are not using the root user. Change the values in red
according to your server’s IP address and SSH port number (the default
number is 22, so try that first unless your server uses a custom port
number).
Once you are logged in, you should update all of your packages to their latest available versions.
apt-get update -y
apt-get upgrade -y
Once all the packages are up-to-date, restart your server to apply
the configuration changes and ensure that all software is running on
their latest versions.
Step 2. Create a System User Account
PostfixAdmin has the ability to create multiple virtual domains,
users and aliases. This saves us the hassle of having to create new
system users whenever we need a new email account added. For security
reasons, we will create a new user named ‘vmail’ with permissions to
store the emails in the /var/vmail directory:
useradd -r -u 150 -g mail -d /var/vmail -s /sbin/nologin -c "Virtual Mail User" vmail
mkdir -p /var/vmail
chmod -R 770 /var/vmail
chown -R vmail:mail /var/vmail
Step 3. Install PHP, Apache and Required Extensions
PHP 7.4 and Apache2 are included in the default Ubuntu repository for
20.04. We can install Apache 2, PHP 7.4 and the required PHP extensions
using the following command. We also included the required PHP and
Apache modules in the command:
apt-get install apache libapache2-mod-php php php-common php-mbstring php-imap php-mysql
Step 4. Install MariaDB Server
PostfixAdmin requires a database in order to be able to store the
email account and domain information. For the purpose of this tutorial,
we will use a MariaDB database system, an open-source version of MySQL
that maintains feature parity. We can install the MariaDB server using
the following command:
apt-get install mariadb-server mariadb-client mariadb-common
Start the MariaDB service and enable it to start on server boot using the following commands:
systemctl start mariadb
systemctl enable mariadb
In order to improve the security of your MariaDB installation, run the mysql_secure_installation script:
mysql_secure_installation
When prompted, you can set the MariaDB root password and safely answer ‘Y’ to all questions.
Enter current password for root (enter for none): Just press the [Enter] key since there is no default password
Set root password? [Y/n]: Y
New password: Enter a strong password
Re-enter new password: Repeat the same password from before
Remove anonymous users? [Y/n]: Y
Disallow root login remotely? [Y/n]: Y
Remove test database and access to it? [Y/n]: Y
Reload privilege tables now? [Y/n]: Y
If you followed the above steps, then you will have a password set for the MariaDB root user.
Run this command to access the MySQL console:
mysql -u root -p
And enter the root password you set previously using the mysql_secure_installation script. If you chose not to run that script, there is no password set, so you just need to press the [Enter] key once.
Next, create a MariaDB user and database for PostfixAdmin:
MariaDB [(none)]> CREATE USER 'postfixadmin'@'localhost' IDENTIFIED BY 'Strong_Password';
MariaDB [(none)]> CREATE DATABASE postfixadmin;
MariaDB [(none)]> GRANT ALL PRIVILEGES ON postfixadmin.* TO 'postfixadmin'@'localhost';
MariaDB [(none)]> FLUSH PRIVILEGES;
MariaDB [(none)]> \q
Do not forget to replace ‘Strong_Password‘ with a good and unique password.
Step 5. Install Postfix
Install Postfix and postfix-mysql packages by running the command below:
apt-get install postfix postfix-mysql
During the Postfix installation, you will be asked for the type of
mail configuration. Select ‘Internet Site’ and click on OK to continue.
Then, enter the server’s hostname in the ‘system mail name’ field.
Once the Postfix installation is complete, we have to create several
Postfix configuration files. This will take a while as there are quite a
few files that have to be made and configured.
mkdir -p /etc/postfix/sql/
Define the database connection settings for querying the virtual alias domain catchall maps by creating this file. We’re using vi, but you can use any text editor that you prefer:
vi /etc/postfix/sql/mysql_virtual_alias_domain_catchall_maps.cf
Once the file is created, insert these contents:
user = postfixadmin
password = Strong_Password
hosts = localhost
dbname = postfixadmin
query = SELECT goto FROM alias,alias_domain WHERE alias_domain.alias_domain = '%d' and alias.address = CONCAT('@', alias_domain.target_domain) AND alias.active = 1 AND alias_domain.active='1'
Create this file so we can set the database connection settings for querying the virtual alias domain mailbox maps:
vi /etc/postfix/sql/mysql_virtual_alias_domain_mailbox_maps.cf
Then insert these contents:
user = postfixadmin
password = Strong_Password
hosts = localhost
dbname = postfixadmin
query = SELECT maildir FROM mailbox,alias_domain WHERE alias_domain.alias_domain = '%d' and mailbox.username = CONCAT('%u', '@', alias_domain.target_domain) AND mailbox.active = 1 AND alias_domain.active='1'
After that, define the database connection settings for querying the virtual alias domain maps by creating this file:
vi /etc/postfix/sql/mysql_virtual_alias_domain_maps.cf
Add the following:
user = postfixadmin
password = Strong_Password
hosts = localhost
dbname = postfixadmin
query = SELECT goto FROM alias,alias_domain WHERE alias_domain.alias_domain = '%d' and alias.address = CONCAT('%u', '@', alias_domain.target_domain) AND alias.active = 1 AND alias_domain.active='1'
The next settings are for the database connection settings for querying the virtual alias maps. Create this file:
vi /etc/postfix/sql/mysql_virtual_alias_maps.cf
Add this text:
user = postfixadmin
password = Strong_Password
hosts = localhost
dbname = postfixadmin
query = SELECT goto FROM alias WHERE address='%s' AND active = '1'
There are a few more to go. Now, create a file for the database connection settings for querying the virtual domain maps:
vi /etc/postfix/sql/mysql_virtual_domains_maps.cf
Make sure you set the passwords on all of these files that you have been adding. Add the contents:
user = postfixadmin
password = Strong_Password
hosts = localhost
dbname = postfixadmin
query = SELECT domain FROM domain WHERE domain='%s' AND active = '1'
Onto the next file. Create it and add the database connection settings for querying the virtual mailbox limit maps:
vi /etc/postfix/sql/mysql_virtual_mailbox_limit_maps.cf
Insert this and change the password:
user = postfixadmin
password = Strong_Password
hosts = localhost
dbname = postfixadmin
query = SELECT quota FROM mailbox WHERE username='%s' AND active = '1'
Finally, create this file and add the database connection settings for querying the virtual mailbox maps:
vi /etc/postfix/sql/mysql_virtual_mailbox_maps.cf
user = postfixadmin
password = Strong_Password
hosts = localhost
dbname = postfixadmin
query = SELECT maildir FROM mailbox WHERE username='%s' AND active = '1'
NOTE: Do not forget to replace ‘Strong_Password‘ with your own password in all of the configuration files above.
Modify the main.cf Postfix configuration file, which is the core of the Postfix configuration. Run these commands to edit each setting:
postconf -e "myhostname = $(hostname -f)"
postconf -e "virtual_mailbox_domains = proxy:mysql:/etc/postfix/sql/mysql_virtual_domains_maps.cf"
postconf -e "virtual_alias_maps = proxy:mysql:/etc/postfix/sql/mysql_virtual_alias_maps.cf, proxy:mysql:/etc/postfix/sql/mysql_virtual_alias_domain_maps.cf, proxy:mysql:/etc/postfix/sql/mysql_virtual_alias_domain_catchall_maps.cf"
postconf -e "virtual_mailbox_maps = proxy:mysql:/etc/postfix/sql/mysql_virtual_mailbox_maps.cf, proxy:mysql:/etc/postfix/sql/mysql_virtual_alias_domain_mailbox_maps.cf"
postconf -e "smtpd_tls_cert_file = /etc/ssl/certs/ssl-cert-snakeoil.pem"
postconf -e "smtpd_tls_key_file = /etc/ssl/private/ssl-cert-snakeoil.key"
postconf -e "smtpd_use_tls = yes"
postconf -e "smtpd_tls_auth_only = yes"
postconf -e "smtpd_sasl_type = dovecot"
postconf -e "smtpd_sasl_path = private/auth"
postconf -e "smtpd_sasl_auth_enable = yes"
postconf -e "smtpd_recipient_restrictions = permit_sasl_authenticated, permit_mynetworks, reject_unauth_destination"
postconf -e "mydestination = localhost"
postconf -e "mynetworks = 127.0.0.0/8"
postconf -e "inet_protocols = ipv4"
postconf -e "inet_interfaces = all"
postconf -e "virtual_transport = lmtp:unix:private/dovecot-lmtp"
We can also install Certbot, then install a new Let’s encrypt SSL certificate for the server hostname and replace /etc/ssl/certs/ssl-cert-snakeoil.pem and /etc/ssl/private/ssl-cert-snakeoil.key with the newly created SSL certificate and public key files.
Then, edit the the master.cf Postfix configuration file, and modify it as follows:
vi /etc/postfix/master.cf
Add or change the contents so that the file looks like this:
smtp inet n - y - - smtpd
#smtp inet n - y - 1 postscreen
#smtpd pass - - y - - smtpd
#dnsblog unix - - y - 0 dnsblog
#tlsproxy unix - - y - 0 tlsproxy
submission inet n - y - - smtpd
-o syslog_name=postfix/submission
-o smtpd_tls_security_level=encrypt
-o smtpd_sasl_auth_enable=yes
# -o smtpd_reject_unlisted_recipient=no
# -o smtpd_client_restrictions=$mua_client_restrictions
# -o smtpd_helo_restrictions=$mua_helo_restrictions
# -o smtpd_sender_restrictions=$mua_sender_restrictions
# -o smtpd_recipient_restrictions=
# -o smtpd_relay_restrictions=permit_sasl_authenticated,reject
-o smtpd_client_restrictions=permit_sasl_authenticated,reject
-o milter_macro_daemon_name=ORIGINATING
smtps inet n - y - - smtpd
-o syslog_name=postfix/smtps
# -o smtpd_tls_wrappermode=yes
-o smtpd_sasl_auth_enable=yes
# -o smtpd_reject_unlisted_recipient=no
-o smtpd_client_restrictions=permit_sasl_authenticated,reject
# -o smtpd_client_restrictions=$mua_client_restrictions
# -o smtpd_helo_restrictions=$mua_helo_restrictions
# -o smtpd_sender_restrictions=$mua_sender_restrictions
# -o smtpd_recipient_restrictions=
# -o smtpd_relay_restrictions=permit_sasl_authenticated,reject
-o milter_macro_daemon_name=ORIGINATING
Enable the Postfix service to start on server boot and restart the Postfix service:
systemctl enable postfix
systemctl restart postfix
Postfix is finally installed and configured.
Step 6. Install Dovecot
Dovecot is a Mail Delivery Agent which allows a user to receive
emails in complete security through IMAP and/or POP3 protocols. We can
install Dovecot and the dovecot-mysql package using the command below:
apt-get install dovecot-core dovecot-lmtpd dovecot-imapd dovecot-pop3d dovecot-mysql
Edit the /etc/dovecot/conf.d/10-mail.conf file:
vi /etc/dovecot/conf.d/10-mail.conf
Insert this as the content:
mail_location = maildir:/var/vmail/%d/%n
mail_privileged_group = mail
mail_uid = vmail
mail_gid = mail
first_valid_uid = 150
last_valid_uid = 150
Open the /etc/dovecot/conf.d/10-auth.conf file:
vi /etc/dovecot/conf.d/10-auth.conf
Edit it so that the file looks like this:
auth_mechanisms = plain login
#!include auth-system.conf.ext
!include auth-sql.conf.ext
Then edit the dovecot-sql.conf.ext file, and add these lines:
vi /etc/dovecot/dovecot-sql.conf.ext
driver = mysql
connect = host=localhost dbname=postfixadmin user=postfixadmin password=Strong_Password
default_pass_scheme = MD5-CRYPT
password_query = SELECT username as user, password, '/var/vmail/%d/%n' as userdb_home, 'maildir:/var/vmail/%d/%n' as userdb_mail, 150 as userdb_uid, 8 as userdb_gid FROM mailbox WHERE username = '%u' AND active = '1'
user_query = SELECT '/var/vmail/%d/%u' as home, 'maildir:/var/vmail/%d/%u' as mail, 150 AS uid, 8 AS gid, concat('dirsize:storage=', quota) AS quota FROM mailbox WHERE username = '%u' AND active = '1'
Do not forget to replace Strong_Password with the actual password that you set previously in Step 4 when creating the MariaDB user.
Edit the /etc/dovecot/conf.d/10-ssl.conf file, and enable SSL support:
vi /etc/dovecot/conf.d/10-ssl.conf
ssl = yes
Save and close that file, then edit the /etc/dovecot/conf.d/15-lda.conf file and set the postmaster_address email address.
vi /etc/dovecot/conf.d/15-lda.conf
postmaster_address = postmaster@yourdomain.com
Make sure that you change yourdomain.com to the actual domain name that points to your server.
Edit the /etc/dovecot/conf.d/10-master.conf file, find the service lmtp section and replace it with the following lines:
vi /etc/dovecot/conf.d/10-master.conf
service lmtp {
unix_listener /var/spool/postfix/private/dovecot-lmtp {
mode = 0600
user = postfix
group = postfix
}
}
Once that part is edited, find the service auth section and replace it with the following snippet:
service auth {
unix_listener /var/spool/postfix/private/auth {
mode = 0666
user = postfix
group = postfix
}
unix_listener auth-userdb {
mode = 0600
user = vmail
}
user = dovecot
}
Then change the service auth-worker section to the following:
service auth-worker {
user = vmail
}
Save and close the file.
Set the correct permissions of the Dovecot configuration files:
chown -R vmail:dovecot /etc/dovecot
chmod -R o-rwx /etc/dovecot
Enable the Dovecot service to start on server boot, and restart
Dovecot so that all of these new configuration files are in effect:
systemctl enable dovecot
systemctl restart dovecot
Step 7. Install PostfixAdmin
Now that all of our required software is installed and configured,
let’s install and configure PostfixAdmin and finish this tutorial.
Download the latest available version of PostfixAdmin from Github and extract it in the /var/www/html/postfixadmin directory.
apt-get install git
cd /var/www/html/
git clone https://github.com/postfixadmin/postfixadmin.git
Edit the /var/www/html/postfixadmin/config.local.php file and add these lines:
vi /var/www/html/postfixadmin/config.local.php
<?php
$CONF['database_type'] = 'mysqli';
$CONF['database_host'] = 'localhost';
$CONF['database_user'] = 'postfixadmin';
$CONF['database_password'] = 'Strong_Password';
$CONF['database_name'] = 'postfixadmin';
$CONF['configured'] = true;
$CONF['encrypt'] = 'md5crypt';
?>
Replace Strong_Password with the MariaDB user password.
mkdir /var/www/html/postfixadmin/templates_c
chown -R www-data: /var/www/html/postfixadmin
Open http://your_server_IP/postfixadmin/public/setup.php . Check if everything is okay and make sure that there are no errors:
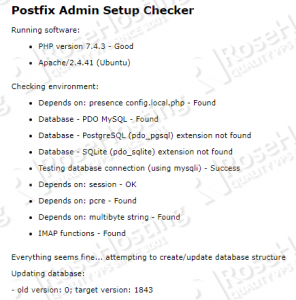
Scroll down and enter your new setup password twice. Make sure to choose a strong one:
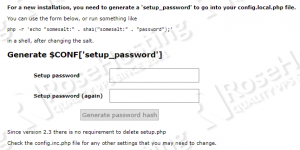
Then click on the ‘Generate password hash’ button.
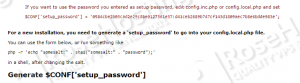
Edit the config.local.php file and add the generated hash to it:
$CONF['setup_password'] = '0584cbe2b03cad2e29c8be0127361e37:d41ceb2689b747cf143d1809aec7b8e6bdde983e';
Replace the hash shown in the example with the one generated for your instance.
Save the config.local.php file, open the setup page once
again and create a PostfixAdmin admin user account. The setup password
in that page is the same password you used in the previous step, so fill
the other required fields such as the admin email address and password,
then click on the ‘Add admin’ button.
That’s it! The PostfixAdmin installation is complete.
Open http://your_server_IP/postfixadmin/login.php in your preferred web browser. You’ll see the login page:
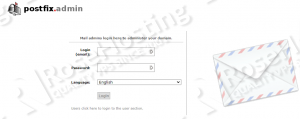
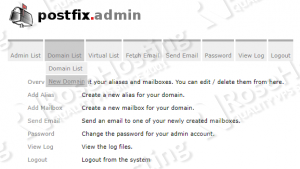
Log in as the admin user and add the domains hosted on the server:
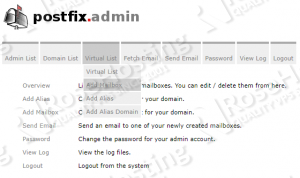
Once you do that, then you can create email addresses, set a mail quota, and so on:
 That is everything you’ll need to install, configure, and start using your PostfixAdmin install on your Ubuntu 20.04 VPS.
That is everything you’ll need to install, configure, and start using your PostfixAdmin install on your Ubuntu 20.04 VPS.
 This
install process is very involved and is quite easy to mess up and end
up with a botched install of Postfix, Dovecot, or both. However, if you
have a Managed Ubuntu VPS hosting
with us, you won’t need to do anything more than ask us to install it
for you, Our team of support experts will completely install and
configure all aspects of your server so that Postfix, Dovecot, and
PostfixAdmin all work flawlessly. They can also help set up routine
maintenance and optimize your server to maximize its speed.
This
install process is very involved and is quite easy to mess up and end
up with a botched install of Postfix, Dovecot, or both. However, if you
have a Managed Ubuntu VPS hosting
with us, you won’t need to do anything more than ask us to install it
for you, Our team of support experts will completely install and
configure all aspects of your server so that Postfix, Dovecot, and
PostfixAdmin all work flawlessly. They can also help set up routine
maintenance and optimize your server to maximize its speed.
We would appreciate you sharing this on social media if you found
this tutorial useful. Or, you can write a comment letting us know how
the install went, and if PostfixAdmin helped you manage your mail server
more easily. Thanks!
Kaynak: https://www.rosehosting.com/blog/how-to-install-a-mail-server-with-postfixadmin-on-ubuntu-20-04











 PostfixAdmin
is an open-source web-based application written in PHP that’s used to
create virtual domains and email accounts for a
PostfixAdmin
is an open-source web-based application written in PHP that’s used to
create virtual domains and email accounts for a 




 That is everything you’ll need to install, configure, and start using your PostfixAdmin install on your Ubuntu 20.04 VPS.
That is everything you’ll need to install, configure, and start using your PostfixAdmin install on your Ubuntu 20.04 VPS. This
install process is very involved and is quite easy to mess up and end
up with a botched install of Postfix, Dovecot, or both. However, if you
have a
This
install process is very involved and is quite easy to mess up and end
up with a botched install of Postfix, Dovecot, or both. However, if you
have a 










